Web and Mobile Development - Digital Signatures
Activity Goals
The goals of this activity are:- To explain and execute the process for public-key cryptography
- To explain how public key cryptography is used to generate a digital signature that enforces non-repudiation
The Activity
Directions
Consider the activity models and answer the questions provided. First reflect on these questions on your own briefly, before discussing and comparing your thoughts with your group. Appoint one member of your group to take notes for the group, and appoint another member to discuss your findings with the class. After class, think about the questions in the reflective prompt and respond to those individually. Report out on areas of disagreement or items for which you and your group identified alternative approaches. Write down and report out questions you encountered along the way for group discussion.Model 1: Public-Key Cryptography
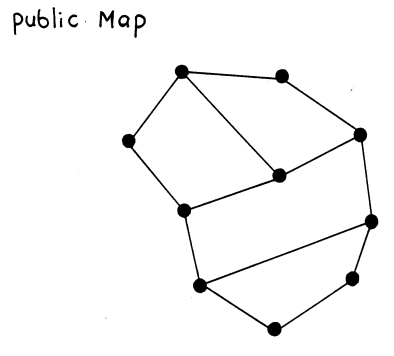
Questions
- Choose a secret numeric value that you want to send securely to a partner.
- Fill in the nodes of the public map with integers that add up to the secret value you chose.
- For each node, replace the value with the sum of itself plus the original value found in the adjacent neighbors.
- Send this graph to your partner. Can your partner figure out the value without any help (probably not!)?
- Your partner (and only your partner) should look at the Private Map (see below), which highlights the nodes that should be added together to obtain the value.
- How did this work? If every student used a unique "map," how could you use this approach to send data securely to anyone?
Model 2: Digital Signatures
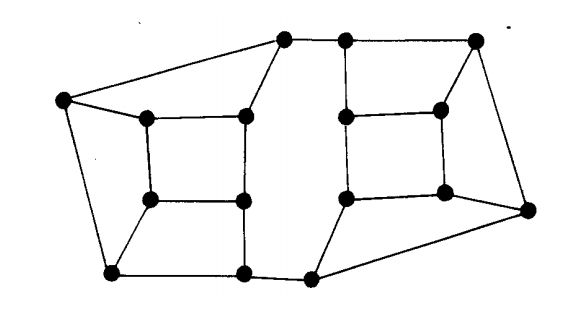
Questions
- If I encrypt something using someone's private map, who can decode it?
- If I encrypt something using my own public map, who can decode it?
- How could you use these maps to ensure that a particular person actually sent a particular value?
- How can I use this approach to ensure that the data that I sent was not altered along the way?
The CS Unplugged Materials are shared by CSUnplugged under a Creative Commons BY-NC-SA 4.0 License.
The Private Map for this activity can be found here and here